HTML Framer Virus
HTML Framer Virus in Wordpress. Hi folks. As promised, here's another in a series of tips and tricks. This one is about how to go about a removing the HTML Framer Virus from a Wordpress installation. I know I promised to cover installation of Wordpress on a live server in this post, but a recent hack on a client's site prompted me to address this issue first. What is the HTML Framer Virus? Well firstly, it's a royal pain in the rear end! After that, it's a malicious chunk of code that infects your theme's header.php file. Essentially, it inserts itself [...]
Tips and Tricks
Tips and Tricks - Strategy, Print, Web, Coding, E-Learning, E-Commerce A happy new year to everyone! I hope that you all had a good holiday and are keen to get back to work! With that purpose in mind, I'm finally about to deliver on a promise I made some time ago. I'm going to create an area on this website purely devoted to helping people get good advice on a number of topics, particularly in the area of design, development and maintenance of websites, mobile applications, e-commerce and e-learning. This will take the form of a Blog, and it'll be a [...]
AshleyMadison Dating Site Hacked
The news that the ashleymadison.com dating site has been hacked probably raises more questions than can easily be answered in a single post. But what it really illustrates is that any company that gets on the wrong side of faceless digi-terrorists with intent, technical knowhow and persistence can be held to ransom. Whether you believe that a dating site like AshleyMadison has a legitimate place in our society or not is irrelevant. What's more important here is the way that the data was siphoned, the way that the company dealt with the threat, and the ramifications for all users of the site. [...]
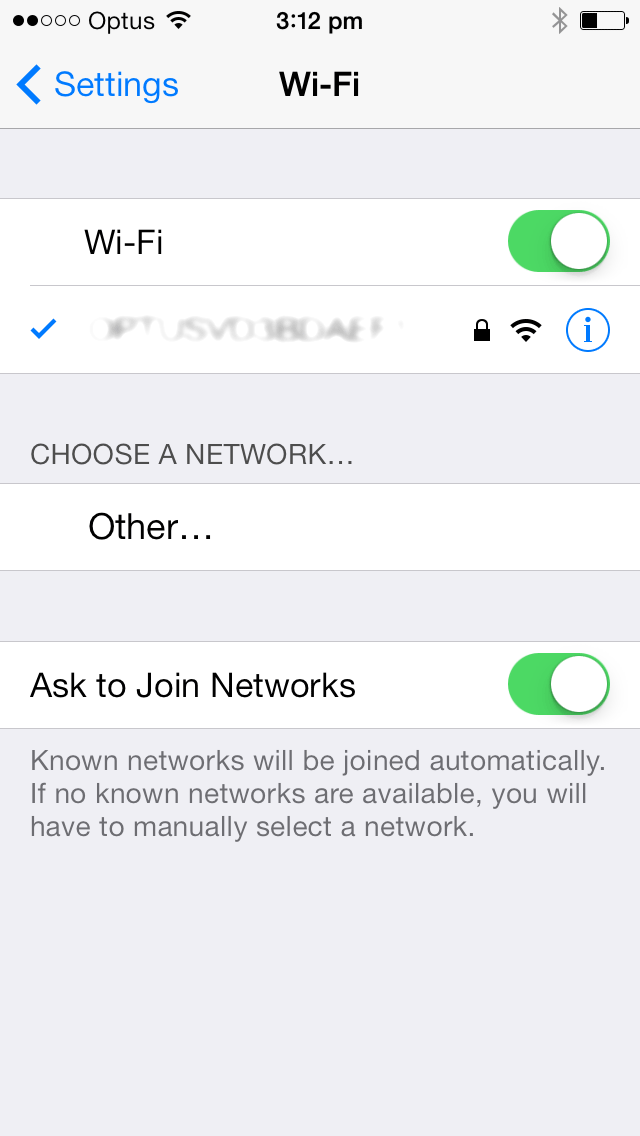
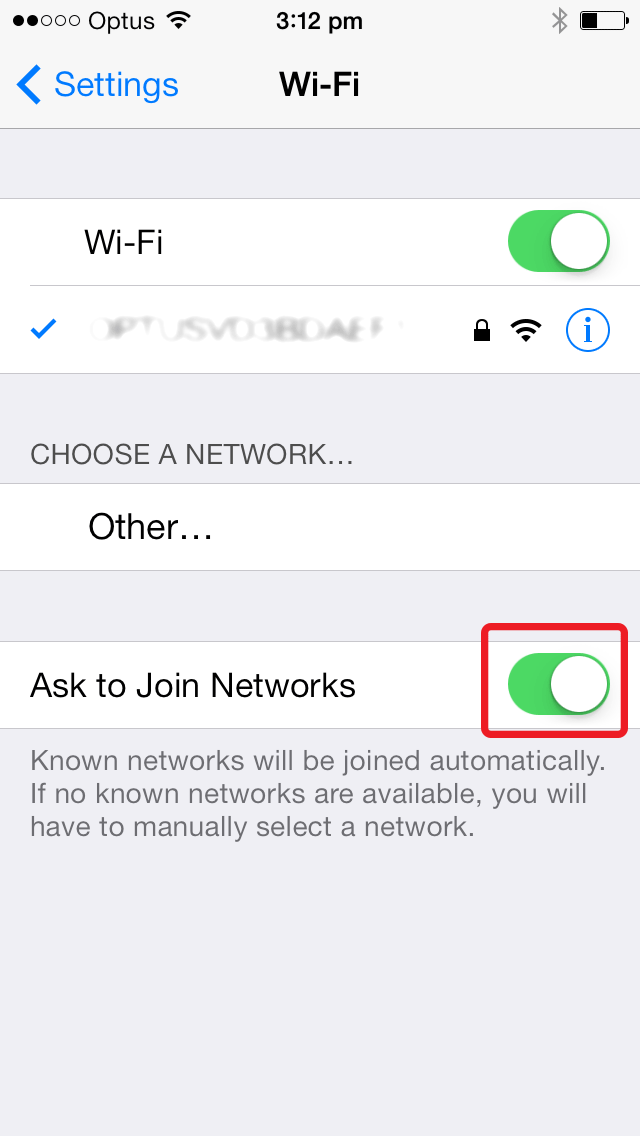
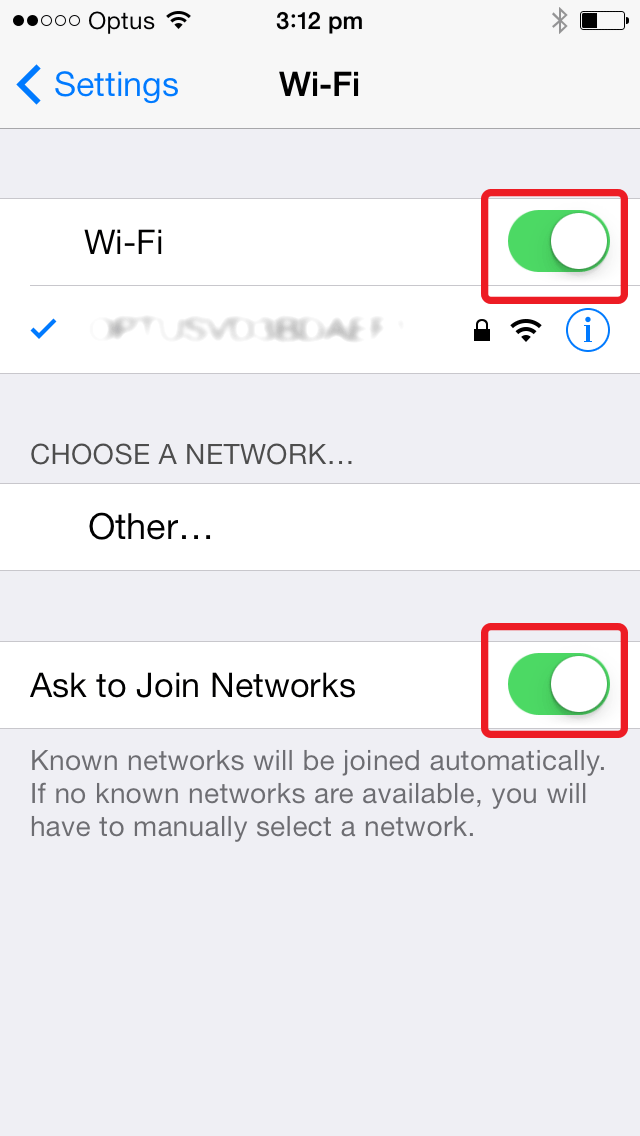
No iOS Zone WiFi attack
No iOS Zone WiFi attack. Imagine this - crossing the street or sitting in a moving taxi and suddenly your phone or iPad reboots. You're puzzled and annoyed, particularly since you may have been on the phone to a client or friend, perhaps in the middle of writing a long text message. So you wait for the phone (or iPad) to finish the reboot process. And then it does it again. And again. Right now, you're beyond annoyed. Almost in throw-the-phone-at-the-wall territory. The guy standing next to you is chatting away happily, but ten feet away, there's another person looking [...]
My website has been hacked!
My website has been hacked - A drama in 4 acts. The plot analysis and author's comment: Perhaps you might think that it's not such a great idea for a web developer to admit that his website has been hacked. We're supposed to be fully conversant with all the strange, weird and nasty ways that people with far too much time on their hands decide to use it. We should be above it, immune, savvy and untouchable. There's the first mistake. The reality is that even the most secure websites can eventually be broken. Just like the unsinkable Titanic, a website can [...]
NSA denies knowledge of Heartbleed Security bug
NSA didn't know about the Heartbleed Security bug - or so they say. Everyone loves a good conspiracy story , so when Bloomberg reported that the NSA had been aware of the potential for exploitation for at least 2 years, the White House and US intelligence agencies replied on Friday that neither the National Security Agency nor any other part of the government were aware before this month of the "Heartbleed" bug. They wholeheartedly deny that the spy agency exploited the glitch in widely used web encryption technology to gather intelligence in order to obtain passwords and other basic information used [...]
Heartbleed Security Bug
Heartbleed Security Bug - Will you be affected? There's been a flurry of news on the web over the last few days about this because clearly some of the major news services needed some front-page pull. The vulnerability has been common knowledge for over a year, and the affected versions have been available for at least two years. Let's get a few things straight before you start running around like headless chooks changing your passwords, moving your Internet Service provider and generally making life difficult for yourself. What is Heartbleed? The Heartbleed Bug is a serious vulnerability in the popular [...]
Devices at risk of hacking
Apple mobile devices could be at risk of hacking A major flaw in Apple software for mobile devices could possibly allow hackers to intercept email and other communications that are meant to be encrypted. If attackers have access to a mobile user's network, such as by sharing the same unsecured wireless service , they could see or alter exchanges between the user and protected sites . Governments with access to telecom carrier data could do the same. Apple did not say when or how it learned of the flaw in the way iOS handles sessions in what are known as [...]
Right to read user emails
Yahoo, Google and Apple claim the right to read user emails. Like Microsoft, other webmail giants all reserve the right to read user emails, if 'deemed necessary'. Microsoft isn't the only one to make the decision - Yahoo, Apple and Google also claim the right. This surfaced following Microsoft's admission that it read a journalist's Hotmail account in an attempt to track down the source of an internal leak. The fact that most webmail services state that they do this to 'protect their property' is not in any way making me feel better about the situation. Yahoo requires users to [...]
Australian Privacy Law
Changes to Australian Privacy Law From 12 March 2014, the Australian Privacy Principles (APPs) will replace the National Privacy Principles and Information Privacy Principles and will apply to organisations, and Australian Government (and Norfolk Island Government) agencies. Here's a quick précis of the new Australian Privacy Principles, taken from the Office of the Australian Information Commissioner website. Part 1 — Consideration of personal information privacy Principle 1 — open and transparent management of personal information Principle 2 — anonymity and pseudonymity Part 2 — Collection of personal information Principle 3 — collection of solicited personal information Principle 4 — dealing with unsolicited [...]














 | © 2014 John Ryan Design | All Rights Reserved | 100 percent Australian |
| © 2014 John Ryan Design | All Rights Reserved | 100 percent Australian |